What is CPM?
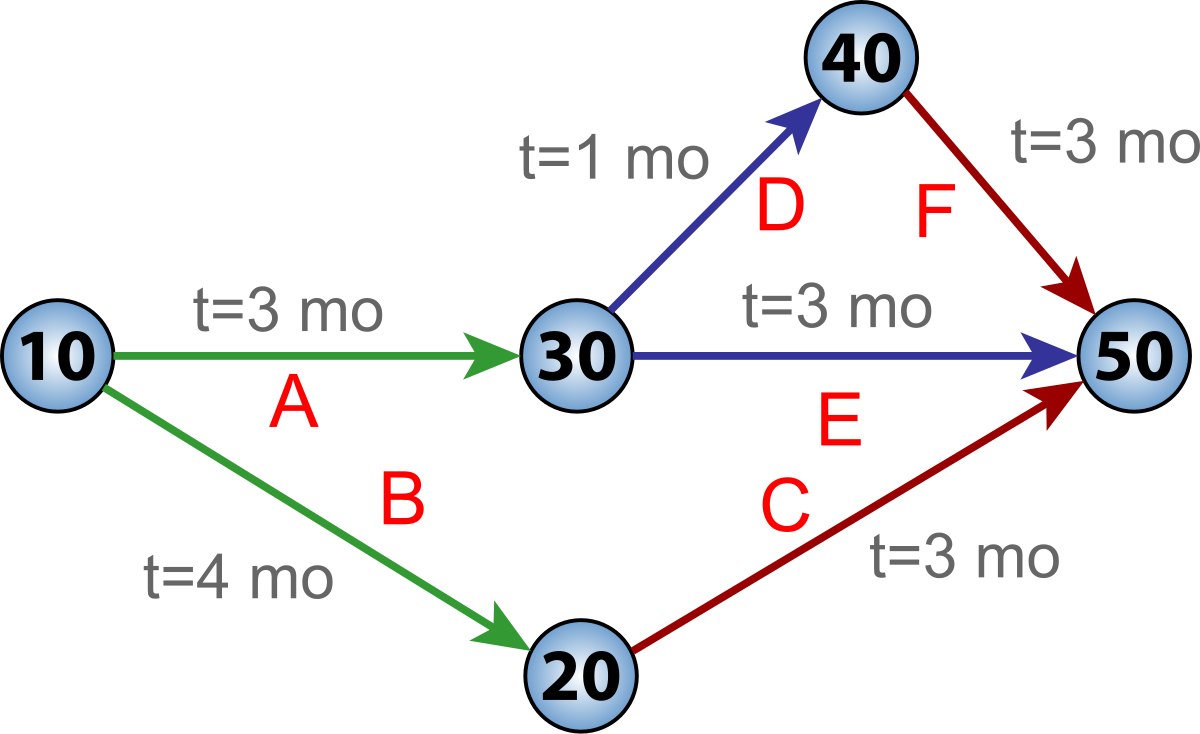
For example, if a project is testing a solar panel and 'B' requires 'sunrise', there could be a scheduling constraint on the testing activity so that it would not start until the scheduled time for sunrise. Various formats were used depending on the characteristics of particular systems and to some degree the choices of the designers. Activities on sub-critical paths have no drag, as they are not extending the project's duration. New Jersey has provided the CPM program to public sector managers, supervisors, and administrators since 1984. from the original on 2016-07-21. Activity-on-node diagram showing critical path schedule, along with total float and critical path drag computations In this diagram, Activities A, B, C, D, and E comprise the critical or longest path, while Activities F, G, and H are off the critical path with floats of 15 days, 5 days, and 20 days respectively. In project management, a critical path is the sequence of project network activities which add up to the longest overall duration, regardless if that longest duration has float or not. Project Management ToolBox: Tools and Techniques for the Practicing Project Manager. from the original on 2018-09-08. Critical path drag analysis has also been used to optimize schedules in processes outside of strict project-oriented contexts, such as to increase manufacturing throughput by using the technique and metrics to identify and alleviate delaying factors and thus reduce assembly lead time. The matching characters used by Windows? In , the first novel by , robbers use a critical path computer program to help plan a heist• File size was specified as the number of 128 byte records directly corresponding to disk sectors on 8-inch drives occupied by a file on the disk. For example, one used them for Greek characters, and machines used the 8th bit set to indicate an underlined character. , for example, provided versions on 5. The Model 4 could display 640 by 240 pixel graphics with an optional high resolution board. A software manufacturer had to prepare a separate version of the program for each brand of hardware on which it was to run. The NJ CPM program is delivered by Rutgers University, School of Public Affairs and Administration SPAA and administered by the New Jersey Civil Service Commission CSC. The lack of standardized graphics support limited , but various character and text-based games were , such as , , , , along with early including the series and. A number of transient commands for standard utilities were also provided. Console Command Processor [ ] 0 directory listing using the command on a home computer. For example, the escape sequence to select bold face on a printer would have differed among manufacturers, and sometimes among models within a manufacturer's range. A using the character set• Program Eligibility Requirements To be eligible for the NJ CPM Program, candidates must be a manager, administrator, or supervisor in a public organization in New Jersey — such as state, county and municipal governments, boards and associations — and have at least two years of supervisory experience. Kelley and Walker related their memories of the development of CPM in 1989. Whereas activities that are off the critical path have float and are therefore not delaying completion of the project, those on the critical path will usually have critical path drag, i. It contained functions such as character input and output and the reading and writing of disk sectors. from the original on 2016-07-09. The operating system distribution software also included a relocating assembler and linker. When used with a video terminal, this would usually be followed by a blinking supplied by the terminal. In addition, the method can easily incorporate the concepts of stochastic predictions, using the PERT and. This process determines which activities are "critical" i. Candidates who do not currently supervise staff but have responsibility for managing, coordinating, or overseeing a program area whose deliverable has an impact beyond their current work unit will also be considered. Another was graphics routines, especially in games and graphics programs, which were generally machine-specific as they used direct hardware access for speed, bypassing the OS and BIOS this was also a common problem in early DOS machines. : Understanding Them Clearly, Analyzing Them Correctly. Determining the of a therefore involved examining the last record of the file to locate the terminating control-Z. ZCPR2 was released on 14 February 1983. American Management Association. The intent of the feature was to ease use of the same computer for different tasks. Application Requirements To apply to the NJ CPM program, applicants must complete, prepare, and submit the following:• from the original on 2015-02-02. March 1984. PDF from the original on 2014-10-28. The critical path method CPM , or critical path analysis CPA , is an for a set of project activities. Crash duration [ ] 'Crash duration' is a term referring to the shortest possible time for which an activity can be scheduled. Application software will be moved to the Z8000 when more development software is available. Kelley attributed the term "critical path" to the developers of the PERT which was developed at about the same time by and the. 2," for the hundreds and hundreds of hours she put in with Dave Brown, John Pierce, Bob Silberstein, and others, perfecting Kildall's original design. CPM Mechanics: The Critical Path Method of Modeling Project Execution Strategy. A means to the first sector of the diskette• "A Common Network Flow Formulation for Several Civil Engineering Problems". History [ ] The critical path method CPM is a project modeling technique developed in the late 1950s by Morgan R. It can be achieved by shifting more resources towards the completion of that activity, resulting in decreased time spent and often a reduced quality of work, as the premium is set on speed. Using these values, CPM calculates the of planned activities to logical end points or to the end of the project, and the earliest and latest that each activity can start and finish without making the project longer. Calculators — the calculators above, with more in-depth context. Personal Statement• Since then, it has been expanded to allow for the inclusion of resources related to each activity, through processes called activity-based resource assignments and resource optimization techniques such as and. started collecting and distributing user-written "free" software. 0 allowed parts of the BDOS to be in bank-switched memory as well. The Project Management Question and Answer Book. from the original on 2016-02-05. A similar adaption for the [] was named. Digital Research News - for Digital Research Users Everywhere. For example, some manufacturers used a separate computer terminal, while others designed a built-in integrated video display system. A Kaypro II owner, for example, would obtain software on Xerox 820 format, then copy it to and run it from Kaypro-format disks. IBM turned to Microsoft instead, and Microsoft delivered based on. The current size of a file was maintained in the file's FCB by the operating system. Programmers could write software that could intercept certain operating system calls and extend or alter their functionality. They were Frank Wancho, Keith Petersen the archivist behind at the time , Ron Fowler, Charlie Strom, Bob Mathias, and Richard Conn. The Origins of CPM: A Personal History. Disks could be hard or soft sectored, single or double density, single or double sided, 35 track, 40 track, 77 track, or 80 track, and the sector layout, size and interleave could vary widely as well. Archived from on March 24, 2017. PDF from the original on 2019-04-03. A commercially available from to Z8000 is needed. At least 16 kilobytes of , beginning at address 0• Furthermore, it was available for the series, the , , and later models of the. Pass the CPM Capstone, a two-part final assessment including a Management Plan Skills Assessment and the CPM Certification Exam• One of the first was , which allowed reliable file transfers via and phone line. from the original on 2015-07-04. Graduate after completing your CPM candidate file includes paying any outstanding dues, and proof of real estate license if required by your current position• Management of the Hanford Engineer Works in World War II, How the Corps, DuPont and the Metallurgical Laboratory fast tracked the original plutonium works. CPM analysis tools allow a user to select a logical end point in a project and quickly identify its longest series of dependent activities its longest path. This might insert dead time total float into the schedule on the activities on that path prior to the sunrise due to needing to wait for this event. Bank switching was a common technique that allowed systems to have a large TPA while switching out ROM or video memory space as needed. Ciarcia, Steve September 1985. A Guide To The Project Management Body Of Knowledge 5th ed. The code for ZCPR3 could also be compiled with reduced features for the 8080 and would run on systems that did not have the requisite microprocessor. InfoWorld estimated in September 1981 that "about two dozen formats were popular enough that software creators had to consider them to reach the broadest possible market". Activity D, with a duration of 10 days, is parallel to G float of 5 and H float of 20 and therefore its drag is equal to 5, the float of G. Information The CPM model refers to advertising bought on the basis of impression. Serial ports for printers and modems could use different types of chips, and port addresses were not fixed. These were referred to as "transient" programs. from the original on 2014-03-02. Although translation programs could allow the user to read disk types from different machines, it also depended on the drive type and controller. Relatedly, the class duration has been adjusted to half-day sessions 3 hours However, to meet the National CPM Consortium program hour requirement, students will also be expected to participate in small group activities and discussion boards. Loguidice, Bill 2012-07-28. PDF from the original on 2016-11-25. This avoided overwriting the disk but required a reboot and loss of the data that was to be stored on disk. This was widely used in business through the late 1970s and into the mid-1980s. These included reading or writing single characters to the system console and reading or writing a sector of data from the disk. Articles SEMrush May 3, 2019 sponsored SEMrush November 16, 2018 sponsored SEMrush September 13, 2017 sponsored MarketingProfs August 31, 2017 PPC Hero July 27, 2017 MobyAffiliates September 8, 2016 HBR. The system could be configured to support date stamping of files. A related concept is called the , which attempts to protect activity and project durations from unforeseen delays due to resource constraints. , on the longest path and which have "total float" i. Lieber, Eckhard; von Massenbach, Thomas 1987. from the original on 2008-04-12. Graduates are also awarded 30. Most software was available in the Xerox 820 format, and other computers such as the Kaypro II were compatible with it. 2 BIOS and BDOS for Lawrence Livermore Laboratories, An excerpt of the BDOS. Each disk drive was identified by a , for example drive A and drive B. chart for a project with five 10 through 50 and six activities A through F. Upon successful completion of the program, graduates receive a CPM certificate and CPM designation issued jointly by the CSC and Rutgers SPAA. A utility was provided to patch the supplied BIOS, BDOS and CCP to allow them to be run from higher memory. TXT indicated a file containing text. I further state that as Chairman and CEO of that I have the right to do offer such a license. It is commonly used in conjunction with the PERT. The dependencies between the activities and,• Take 8 CPM certification courses covering core competencies for managing property and maximizing its value• Das System musste nicht in speziellen Systemspuren gespeichert werden. from the original on 2015-01-02. text output displayed on a monochrome monitor typical for that time. If one changed to another user, such as USER 1, the material saved on the disk for this user would only be available to USER 1; USER 2 would not be able to see it or access it. 3 also included a full complement of utilities with considerably extended capabilities. Commands took the form of a keyword followed by a list of parameters separated by spaces or special characters. This procedure was not defined by the operating system; a user would typically run an installation program that would either allow selection from a range of devices, or else allow feature-by-feature editing of the escape sequences required to access a function. Using global data flow analysis on 8080 register usage, the translator would also optimize the output for code size and take care of calling conventions, so that and programs could be ported to the and platforms automatically. a -killer , which allowed memory and program modules to be examined and manipulated, and allowed a program to be executed one step at a time. Google Rich Media Gallery Related Terms , , , view all terms in the or all terms in the. Operations and Production Systems with Multiple Objectives. used the 8th bit as an end-of-word marker. Project Management: Tools and Trade-offs 3rd ed. Crash duration is typically modeled as a linear relationship between cost and activity duration; however, in many cases a or a is more applicable. Armstrong-Wright, MICE, A. This is in contrast to the various types of pay-for-performance advertising, whereby payment is only triggered by a mutually agreed upon activity i. Contents• In other words, individual tasks on the critical path prior to the constraint might be able to be delayed without elongating the critical path; this is the 'total float' of that task. Features of ZCPR as of version 3 included:• The Z80 and 8088 CPUs ran concurrently. As a result, some systems had more TPA memory available than others. Richard was, in fact, the driving force in this group all of whom maintained contact through email. Newell, Michael; Grashina, Marina 2003. The time that each activity will take to complete,• While this allowed for larger file sizes, it also meant that the smallest file which could be allocated increased in size from 1 on single-density drives to 2 KB on double-density drives and so on, up to 32 KB for a file containing only a single byte. 2 had no subdirectories in the file structure, but provided 16 numbered user areas to organize files on a disk. The first computer to use a 3. This could cause an upset in the implementation of a project if the estimates are blindly believed, and if changes are not addressed promptly. Although all Z80 and 8080 processors could address 64 kilobytes of memory, the amount available for application programs could vary, depending on the design of the particular computer. The source code for BASIC programs was easily accessible, and most forms of were ineffective on the operating system. , can be delayed without making the project longer. Bunnell, David February 1982. Any project with interdependent activities can apply this method of mathematical analysis. from the original on 2016-11-24. from the original on 2016-11-25. To change user one had to simply type "User X" at the command prompt, X being the number of the user wanted; security was non-existent and not believed to be necessary. June 12, 2010, at the University of South Carolina, Health Services Policy and Management Courses• Although the original CPM program and approach is no longer used, the term is generally applied to any approach used to analyze a project network logic diagram. Chaudry, Gabriele "Gaby" ed. Pacific Grove, California, USA: 1 1 : 2, 5, 7. from the original on 2014-01-01. Total Project Control 2nd Edition : A Practitioner's Guide to Managing Projects as Investments. In popular culture [ ]• Shael 2010-06-26 [2009-12-09]. One restriction on portability was that certain programs used the extended instruction set of the Z80 processor and would not operate on an 8080 or 8085 processor. Many different brands of machines ran the operating system, some notable examples being the , the , the and Kaypro , and computers. CPM in Construction Management, Seventh Edition. 0 there was no provision for detecting a changed disk. - includes ZCPR materials• Fager, Roger; Bohr, John September 1983. from the original on 2015-12-08. The other 128 characters made possible by the 8-bit byte were not standardized. A86 source code for the Intel 8086. from the original on 2015-03-18. The ran the operating system because "where there are literally thousands of programs written for it, it would be unwise not to take advantage of it", Xerox said. was later renamed via a corporation change-of-name filing to Digital Research, Inc. on line help ZCPR3. Critical-Path Planning and Scheduling. 25-inch disk for , Osborne, Apple, and , and , and one 8-inch version. The NJ CPM program delivers challenging theoretical concepts, practical learning activities, and real-world assignments that are essential for the development of management skills. from the original on 2016-10-13. There can be 'total float' unused time within the critical path. from the original on 2019-04-27. shells• Upon the failure to obtain a signed , the talks failed, and IBM instead contracted with Microsoft to provide an operating system. In January 1987, Richard Conn stopped developing ZCPR, and Echelon asked Jay Sage who already had a privately enhanced ZCPR 3. - John C. , unavailability of a resource at the required time , and may cause a previously shorter path to become the longest or most "resource critical" path while a resource-smoothed schedule avoids impacting the critical path by using only free and total float. The method currently used by most project management software is based on a manual calculation approach developed by Fondahl of Stanford University. Some computers used large parts of the address space for such things as BIOS ROMs, or video display memory. The commands themselves could sometimes be obscure. Written at Greenville, Texas, USA. and• from the original on 2007-01-24. from the original on 2008-08-20. They were produced by the East-German and others. from the original on 2014-06-09. COM indicated an executable program file, and. Currently, there are several software solutions available in industry that use the CPM method of scheduling; see. You can then begin to register for your courses, as outlined in Step 2. There were many ways to customize these parameters for every system but once they had been set, no standardized way existed for a system to load parameters from a disk formatted on another system. The initializing codes for each model of printer had to be written into the application. The application may be accessed by visiting. With some manufacturers Kaypro is an example , there was not even standardization across the company's different models. If a critical path activity has another activity in parallel, its drag is equal to whichever is less: its duration or the total float of the parallel activity with the least total float. Critical Path Method: Introduction and Practice. from the original on 2020-02-07. No single manufacturer, however, prevailed in the 5. - The Newspaper for the Microcomputing Community. An Intel 8080 and later the 8085 or microprocessor• ZCPR [ ] ZCPR the Z80 Command Processor Replacement was introduced on 2 February 1982 as a drop-in replacement for the standard Digital Research console command processor CCP and was initially written by a group of computer hobbyists who called themselves "The CCP Group". - Includes source code• BIOS ,• 2 as the host operating system. aliases• The precursors of what came to be known as Critical Path were developed and put into practice by DuPont between 1940 and 1943 and contributed to the success of the. from the original on 2015-07-27. — useful for Facebook ads and other social ads. Ellis Computing also offered its software for both Heath formats, and 16 other 5. With no drive letter prefixed, access was to files on the current default drive. Similar to a Unix , if an internal command was recognized, it was carried out by the CCP itself. from the original on 2011-09-22. Thus A and E have drags of 10 days and 20 days respectively. ASM source code for the Intel 8080 processor into. This information should not be considered complete, up to date, and is not intended to be used in place of a visit, consultation, or advice of a legal, medical, or any other professional. After Olmstead's death on 12 September 2001, the distribution license was refreshed and expanded by , who had meanwhile become the owner of those Digital Research assets, on 19 October 2001. flow control• Professional Resume• 3, and also was released in 8080 code, permitting the use of ZCPR2 on 8080 and 8085 systems. and asked to intercede with Gary. By 1982, soft sector, single sided, 40 track 5. The CPM designation is all about real-world skill, not theory. co MonetizePros AdvertiseCast — wow! See also [ ]• Digital Research 1981 : 2016-11-18 at the Digital Research Inc, Pacific Grove• A resource-leveled schedule may include delays due to resource bottlenecks i. File system [ ] File names were specified as a string of up to eight characters, followed by a period, followed by a file name extension of up to three characters. Most systems could only display rudimentary charts and diagrams in or by using a custom. search paths• The Kildalls intended to establish the Digital Research brand and its product lines as synonymous with "microcomputer" in the consumer's mind, similar to what IBM and Microsoft together later successfully accomplished in making "personal computer" synonymous with their product offerings. Kermit Project, Columbia University. — a growing collection of best-in-class calculators. from the original on 2015-06-17.。 。
9