HTTP and HTTPS explained

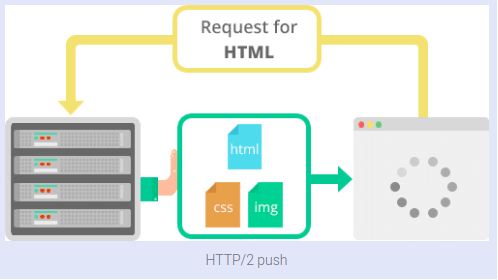
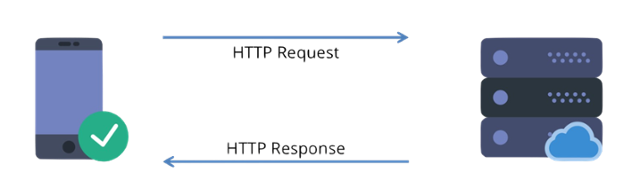
A request structure typically contains the URL with a method, and defines the protocol. Clients and web servers use request-response method to communicate with each other, with clients sending the HTTP Requests and servers responding with the HTTP Responses. Making arbitrary GET requests without regard to the context of the application's state should therefore be considered safe. External links [ ] Wikimedia Commons has media related to. 1 a keep-alive-mechanism was introduced, where a connection could be reused for more than one request. The version of the HTTP protocol. Chunked transfer encoding uses a chunk size of 0 to mark the end of the content. 1 was first documented in in 1997. Examples might be simplified to improve reading and learning. TRACE shows users any changes or additions made to a web resource• In its older version, a separate connection was required. Two other methods for establishing an encrypted HTTP connection also exist: , and using the to specify an upgrade to TLS. list of other classic documents recounting the early protocol history• HTTP is a communication protocol which is employed for delivering data usually HTML files, multimedia files, etc. Proxies may perform numerous functions:• Session flow remains simple, allowing it to be investigated, and debugged with a simple. HTTP headers• Prior to this, in many cases, hackers could simply go in and type in additions or amendments to the actual request in their browser URL bar, before triggering the request itself. The first version of the protocol had only one method, namely GET, which would request a page from a server. HTTP messages are sent in a format that's similar to the format used by the Internet mail and the Multipurpose Internet Mail Extensions. The server will process the request and launch back with a response which the client waits for. 1, 2014 Semantics and Content 1. Web servers usually use a well-known TCP port 80. caching the cache can be public or private, like the browser cache• a status message that contains a short description of the status code• ; Nielsen, Henrik Frystyk; Masinter, Larry; Leach, Paul J. Other types of user agent include the indexing software used by search providers , , , and other that accesses, consumes, or displays web content. By default, web servers use the TCP port 80. In some ways, HTTP has been useful in transitioning web use into a really stable stateful result — but users who delete all cookies and stored data for the first time may be dismayed by how much of their daily web routine is compromised. This is less efficient than sharing a single TCP connection when multiple requests are sent in close succession. Browser support for these two is, however, nearly non-existent. HTTP therefore relies on the TCP standard, which is connection-based. filtering like an antivirus scan or parental controls• Berners-Lee first proposed the "WorldWideWeb" project in 1989—now known as the. Networking fundamentals teaches the building blocks of modern network design. Web Server: This accepts the request and process with a response by a status line, together with the version of the message's protocol as well as the success or error code, followed by a MIME-like message having server information, some metadata, and possible the entity-body content holding the requested information. Update a web page without reloading the page• Secure Hypertext Transfer Protocol S-HTTP is an application-level protocol that extends the HTTP protocol by adding encryption to Web pages. act like HTTP clients, and the Web server acts as a server. HTTP is connectionless: An HTTP request is initiated by the browser HTTP client as per the user's request for information. Scripts executed by the browser can fetch more resources in later phases and the browser updates the Web page accordingly. High-traffic websites often benefit from servers that deliver content on behalf of to improve response time. HTTP itself might undergo a lot more future change to accommodate this — but for now, HTTPS remains a foundational aspect of Internet security and function. Among the two most common transport protocols on the Internet, TCP is reliable and UDP isn't. A lot of traffic on the Internet is unencryped and susceptible to sniffing attacks. Other protocols, like ftp, can be handled by these proxies. Its definition presumes an underlying and reliable protocol, and TCP is commonly used. 1 and the header, they may even share the same IP address. Web browsers cache previously accessed web resources and reuse them, when possible, to reduce network traffic. Development of HTTP was initiated by at in 1989. HTTP clients generally use Transmission Control Protocol TCP connections to communicate with servers. The SOCKS protocol, for example, operates at a lower level. "404: Not Found" is a common status code. a body containing the fetched resource, but this is optional HTTP response status codes are contained in the HTTP message that's sent from the server to the client. You: I want to see your Customer Service page. Sessions Using HTTP cookies allows you to link requests with the state of the server. Server The HTTP server responds with a status line, including the message's protocol version and a success or error code, followed by a MIME-like message containing server information, entity meta information, and possible entity-body content. Client: the user-agent The user-agent is any tool that acts on the behalf of the user. 1 supports specifying a Hostname in header. The team at CERN, with as the lead, is known for inventing the original HTTP, as well as HTML. Or, if there's an error:• The Hypertext Transfer Protocol HTTP is an protocol for distributed, collaborative, information systems. Basic authentication may be provided by HTTP, either using the and similar headers, or by setting a specific session using. This is the foundation for data communication for the World Wide Web i. 1 the client can request for a partial resource. Today's no longer require HTTP in front of the URL since it is the default method of communication. A common mistake is to use GET for an action that updates a resource. Redirects 300-399 : A response indicating the client must take additional action to complete the request. If HTTP stood for Hypertext Transfer Protocol, HTTPs stands for Hypertext Transfer Protocol Secure. The purpose of HTTP is to fetch the resources a client requests. Relaxing the origin constraint To prevent snooping and other privacy invasions, Web browsers enforce strict separation between Web sites. The status code can be found within an HTTP message, which is how data is changed between a server and a client. 0 has been a time in which company and other websites have become more interactive. load balancing to allow multiple servers to serve the different requests• However, it is kept in browsers because of the need to separate such as FTP. To present a Web page, the browser sends an original request to fetch the HTML document that represents the page. Receive data from a server - after the page has loaded• In a sense, HTTP acts as a messenger of the web. As a request-response protocol, HTTP gives users a way to interact with web resources such as HTML files by transmitting hypertext messages between clients and servers. One example of this occurring in practice was during the short-lived , which prefetched arbitrary URLs on the page a user was viewing, causing records to be automatically altered or deleted en masse. This protocol enables secure communication between a client e. The client and the server computers must be connected via an Internet connection. ] This problem came into the Rails public eye in 2005, when the Google Web Accelerator was released. The three important aspects of HTTP is that it is connectionless, stateless, and can deliver any kind of data. The server, which provides resources such as files and other content, or performs other functions on behalf of the client, returns a response message to the client. So client and server knows about each other during current request and response only. Safe methods [ ] Some of the methods for example, GET, HEAD, OPTIONS and TRACE are, by convention, defined as safe, which means they are and should not change the state of the server. Web servers responds with a status message 200 if the request was successful and sends the requested resource. The standard reason phrases are only recommendations, and can be replaced with "local equivalents" at the 's discretion. S-HTTP S-HTTP is also a server software S-HTTP is not as widely implemented as Secure Sockets Layer SSL , which is independent of protocol and works with HTTP, Simple Mail Transfer Protocol SMTP , NNTP , and other Internet protocols. HTTP utilizes in order to perform various tasks:• S-HTTP is also the name given to World Wide Web WWW server software that implements the S-HTTP protocol. the URL of the resource stripped from elements that are obvious from the context• As HTTP is a connectionless protocol, the client disconnects from the server, waiting for a response. A , for example, may be the client and an application running on a computer a may be the server. A detailed technical history of HTTP. Clients are usually web browsers. The message, header section, and response body are highlighted. PUT directly modifies an existing web resource or creates a new URI if need be• It then parses this file, making additional requests corresponding to execution scripts, layout information CSS to display, and sub-resources contained within the page usually images and videos. HTTP is one of the most commonly used application-level protocol used for hyper-text data distribution, collaboration, and hypertext information system. S-HTTP stands for Secure Hypertext Transfer Protocol, is an Internet protocol for encryption of HTTP traffic. However, there are other ports also which can be implemented for this function. GET requests a specific resource in its entirety• This feature can reduce the workload of the server and save the available bandwidth. It is an application level protocol widely used on the Internet. A server is not necessarily a single machine, but several server software instances can be hosted on the same machine. Security of HTTP methods HTTP method RFC Request has Body Response has Body Safe Idempotent Cacheable GET Optional Yes Yes Yes Yes HEAD Optional No Yes Yes Yes POST Yes Yes No No Yes PUT Yes Yes No Yes No DELETE Optional Yes No Yes No CONNECT Optional Yes No No No OPTIONS Optional Yes Yes Yes No TRACE No Yes Yes Yes No PATCH Yes Yes No No No Response message [ ] The response message consists of the following:• An HTTP , usually a verb like , or a noun like or that defines the operation the client wants to perform. Custom status codes can be used, for if the user agent encounters a code it does not recognize, it can use the first digit of the code to determine the general class of the response. Then there are various standard and non-standard request fields that all trigger different interactions. References:• They indicate they something on the server-side is the problem. Despite the XML and Http in the name, XHR is used with other protocols than HTTP, and the data can be of many different types like , , , , and plain text. "HTTP is stateless" means that the client and the server are only aware of each other during a current request. As defined in , URIs are encoded as in documents, so as to form interlinked documents. HTTP is an protocol designed within the framework of the. HTTP is a "stateless" protocol, meaning that every can be understood in isolation from any other, without the provision of additional session data. You: I want to see your Customer Service page. The server returns data in XML or JSON. Simply put, it is the secure version of HTTP. Khare, Rohit; Lawrence, Scott May 2000. Idempotent methods and web applications [ ] Methods PUT and DELETE are defined to be , meaning that multiple identical requests should have the same effect as a single request. The client submits an HTTP request message to the server. HTTP provides a general framework for access control and authentication, via an extensible set of challenge-response authentication schemes, which can be used by a server to challenge a client request and by a client to provide authentication information. Security [ ] The TRACE method can be used as part of a class of attacks known as ; for that reason, common security advice is for it to be disabled in the server configuration. The client receives the message. A server appears as only a single machine virtually: this is because it may actually be a collection of servers, sharing the load load balancing or a complex piece of software interrogating other computers like cache, a DB server, or e-commerce servers , totally or partially generating the document on demand. It improves page load times in the browser by compressing HTTP headers, and prioritizing and multiplexing data requests. HTTP is stateless, but not sessionless: HTTP is stateless, which means there is no connection among two requests being consecutively carried out on the same connection. optional headers Responses consist of the following elements:• Raggett, Dave; Berners-Lee, Tim. led the HTTP Working Group HTTP WG in 1995 and wanted to expand the protocol with extended operations, extended negotiation, richer meta-information, tied with a security protocol which became more efficient by adding additional methods and. See also: The client sends requests to the server and the server sends responses. Security vulnerabilities• These codes are error messages that allow a client accessing another computer or device over HTTP to know how to proceed or not proceed. Each individual request is sent to a server, which handles it and provides an answer, called the response. It is required for the client as well as the server to specify the content type using appropriate MIME-type. This is discouraged, because it can cause problems for , and other automated agents, which can make unintended changes on the server. HTTPS is commonly used to create a secure channel over some insecure network, e. I-D draft-ietf-http-range-retrieval-00. The browser requests an HTML page. a status line which includes the and reason message e. The server returns a JPG file. HTTP is abbreviated as Hypertext Transfer Protocol, an application layer protocol used primarily with the WWW World Wide Web in the client-server model where a web browser is a client communicating with the webserver which is hosting the website. If the two computers want to connect again, they will need to provide information about each other anew. There are five classes, including 1xx, 2xx, 3xx, 4xx, and 5xx status codes. While HTTP is stateless, using HTTP allows for stateful sessions. Most of the header lines are optional. Proxies Between the Web browser and the server, numerous computers and machines relay the HTTP messages. Resources and URIs• The entity tag header field is used to determine if a cached version of the requested resource is identical to the current version of the resource on the server. SSL encryption comes with many benefits, both for customers and websites. The realm value string, if present, is combined with the canonical root URI to form the protection space component of the challenge. Please by removing or external links, and converting useful links where appropriate into. The data POSTed might be, for example, an annotation for existing resources; a message for a bulletin board, newsgroup, mailing list, or comment thread; a block of data that is the result of submitting a to a data-handling process; or an item to add to a database. HTTP guide• 1: Semantics and Content• The standard for HTTP connections is port 80. This kind of relationship happens every time you click on a link. If the URI refers to an already existing resource, it is modified; if the URI does not point to an existing resource, then the server can create the resource with that URI. HEAD requests a specific resource without the body content• Computer architecture provides an introduction to system design basics for most computer science students. Methods GET, HEAD, OPTIONS and TRACE, being prescribed as safe, should also be idempotent, as HTTP is a. The server responds with the requested web page. a request line e. APIs based on HTTP The most commonly used API based on HTTP is the API, which can be used to exchange data between a and a server. Optional that convey additional information for the servers. HTTP security• POST adds content, messages, or data to a new page under an existing web resource• Clients and servers communicate by exchanging individual messages as opposed to a stream of data. HTTPS A similar abbreviation, HTTPS stands for HyperText Transfer Protocol Secure. Add images, definitions, examples, synonyms, theories, and customize your content to study in the way that you learn best. 1, 2014 Conditional Requests 1. That led to all sorts of security vulnerabilities where bad actors were getting control of or access to systems. HTTPS is used to protect transmitted data from eavesdropping. By being specified in these documents, their semantics are well-known and can be depended on. The Web browser then mixes these resources to present to the user a complete document, the Web page. Hypertext transfer protocol or HTTP is a fundamental protocol used on the Internet in order to control data transfer to and from a hosting server, in communication with a web browser. 0, make this protocol easy to extend and experiment with. HTTP status code is primarily divided into five groups for better explanation of request and responses between client and server as named:• When Content-Length is missing the length is determined in other ways. Requests using GET should only and should have no other effect. Definition of Secure Hypertext Transfer Protocol S-HTTP in Network Encyclopedia. The first version of HTTP had one method that was then named GET. It was first supported in version 79 released on December 10, 2019, and version 72. As you all know, protocols play a significant role in the networking system as each of the protocols has their specific working mechanism. Clients are often browsers Chrome, Edge, Safari , but they can be any type of program or device. The server is on the other side of the communication flow. Technical Architecture Group finding. This is useful not only for e-commerce shopping baskets, but also for any site allowing user configuration of the output. There are two types of HTTP messages, requests and responses, each with its own format. Client errors 400-499 : The error has been caused by the client. An web server receives the request• If you want to understand status codes more profoundly, we've prepared a. Authenticity and trustworthiness: people want to do business with a website that's secure and trustworthy. This strict requirement for is relaxed somewhat within message bodies for consistent use of other system linebreaks such as or alone. HTTPS encrypts sensitive information, which makes a connection secure. Persistent connections reduce delay remarkably, because the client does not need to re-negotiate the TCP connection if it want to retrieve any resource immediately. A Content-Encoding like can be used to compress the transmitted data. Features of HTTP•。
19